{Insights}
Feb 4, 2026
by alchemain team
FedRAMP has a reputation problem. For some teams, it’s a mysterious acronym that shows up late in procurement and ruins everyone’s week. For others, it’s a looming compliance mountain that feels unnecessarily complicated.
The reality is that FedRAMP can’t be checked off your to-do list in a single sitting. It’s rigorous, demanding, and assessors are very specific about what “good” looks like. Let’s start by demystifying what FedRAMP actually is, who needs to care, and why seemingly small things like software dependencies can make or break your compliance story.
Spell It Out For Me: What is FedRAMP?
FedRAMP (Federal Risk and Authorization Management Program) is a U.S. government program that standardizes how cloud services are assessed, authorized, and continuously monitored for security when used by federal agencies.
Back in the day, before FedRAMP was established, each federal agency evaluated cloud providers independently. This led to duplicated effort, inconsistent security standards, and slower adoption of crucial standards. FedRAMP solves this by creating a single, rigorous security framework based on NIST standards that all participating cloud service providers (CSPs) must follow.
To achieve FedRAMP authorization, a cloud provider undergoes an extensive security assessment by an accredited third-party assessor (3PAO). This includes documentation, testing of security controls, and risk evaluation. Once authorized, the provider can offer its services to federal agencies without repeating the full process for each one, though ongoing monitoring and reporting are mandatory to maintain approval.
In practice, FedRAMP enables agencies to adopt cloud services faster while maintaining strong security assurance. For vendors, it is often a prerequisite for selling cloud products to the U.S. federal government and is widely seen as a benchmark for enterprise-grade cloud security beyond the public sector.
Who Needs to Think about FedRAMP?
You need to worry about FedRAMP if you fall into one of these groups:
🏛️ U.S. federal agencies: Any federal agency using cloud services must use FedRAMP-authorized offerings. Program offices, CISOs, procurement teams, and security teams are directly accountable for compliance.
☁️ Cloud service providers (CSPs): If you sell SaaS, PaaS, or IaaS to the U.S. federal government, FedRAMP is unavoidable. This includes startups and commercial vendors whose products might otherwise seem “non-government.” Without FedRAMP authorization, most agencies cannot buy or deploy your service.
🔗 Vendors with federal customers’ data in scope: You may need to worry about FedRAMP even if you don’t sell to the government directly. If your software, hosting platform, monitoring tool, or managed service processes, stores, or transmits federal data on behalf of a FedRAMP-authorized provider, you can become part of their compliance boundary.
🧪 Third-party assessors and compliance partners: If your job is to help other companies get or keep FedRAMP approval, then FedRAMP also governs you. Organizations accredited as 3PAOs, along with consultants supporting authorization and continuous monitoring must follow strict program rules.
The Link Between FedRAMP and Dependency Management
We speak to a lot of customers who are struggling with dependency management as part of their FedRAMP compliance roadmap. Software dependencies are part of what FedRAMP assessors consider your system, and if you don’t control dependencies, you can’t credibly claim that you’re compliant. Here’s what we mean.
First up, FedRAMP requires total system visibility, the ability to document and secure everything that runs in your environment. That includes open-source libraries, transitive dependencies, runtime frameworks, and any build-time tooling which ships in production. Vulnerable library in your dependency tree? FedRAMP doesn’t differentiate between that and vulnerable code your developers wrote with their own two hands.
Detection is your first headache, but it isn’t where FedRAMP steps off the gas. FedRAMP assessors want to see control as well as visibility. That means answering questions like:
Do you know which dependencies are in production?
Can you trace a vulnerability to affected systems?
Can you remediate safely without breaking mission systems?
“Dependabot opened a PR for us” is not enough. You need to be able to present evidence of impact analysis, testing and validation.
For many, the challenge starts when you realize FedRAMP isn’t a pass once and put it behind you kind of regulation. It requires ongoing vulnerability scanning, monthly reporting, and rapid remediation timelines. In short — a new CVE in a transitive dependency can put you out of compliance in real-time, even if no new code was deployed. Dependency drift was always a security risk, but now it’s a compliance risk, too.
00felix for FedRAMP Planning and Execution
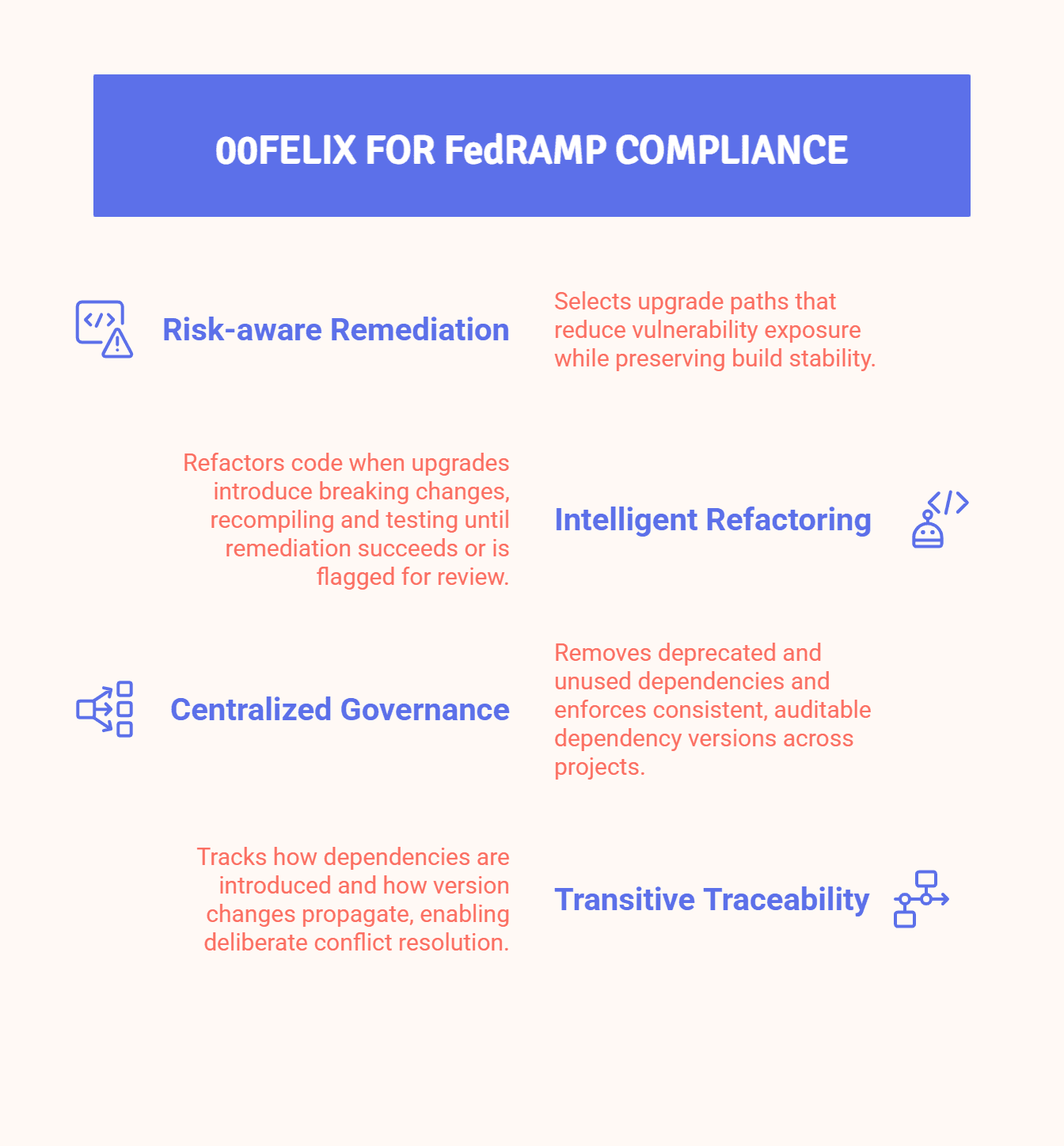
Under FedRAMP, remediation is about making defensible, low-risk decisions and being able to prove them to an assessor. This is where 00felix delivers value that traditional dependency tools don’t.
When a vulnerable transitive dependency is identified, there are often multiple valid remediation paths: upgrading a top-level dependency, unpinning and rebasing, or changing how the dependency is introduced. FedRAMP assessors expect teams to justify their approach and how it reduces risk without introducing operational instability. Most tools provide no help here. They flag the issue and leave teams to figure out the rest.
00felix closes that gap by combining full dependency-graph analysis with outcome validation. It doesn’t just suggest a version bump; it proves that any proposed remediation will work in your actual environment.
For FedRAMP purposes, this matters because every change must be safe. 00felix validates remediation by running the full build and test pipeline, including JDK compatibility and unit tests, before a PR is ever opened. That provides concrete evidence that the fix won’t break the system, which is something assessors care about deeply in mission-critical environments.
If an upgrade would otherwise fail, 00felix can refactor application code to restore compatibility, enabling secure remediation instead of deferral. This supports continuous monitoring by preventing recurring findings caused by “unfixable” dependencies.
The result is a remediation process that is repeatable, auditable, and explainable, terms which describe exactly what FedRAMP expects when evaluating ongoing risk management.
Need some help with your FedRAMP roadmap? Let’s talk.



